Introduction
A major shift is unfolding in the cyber threat landscape. Generative AI is no longer only accelerating attacker workflows. In at least one documented case, it became a core operational engine for a coordinated intrusion campaign.
In November 2025, Anthropic reported that it detected and disrupted what it described as the first documented AI-orchestrated cyber espionage campaign. The case centers on the misuse of Claude Code, with the model executing most operational steps and human operators intervening primarily at strategic points.
The diagram below shows the different phases of the attack, each of which required all three of the above developments:
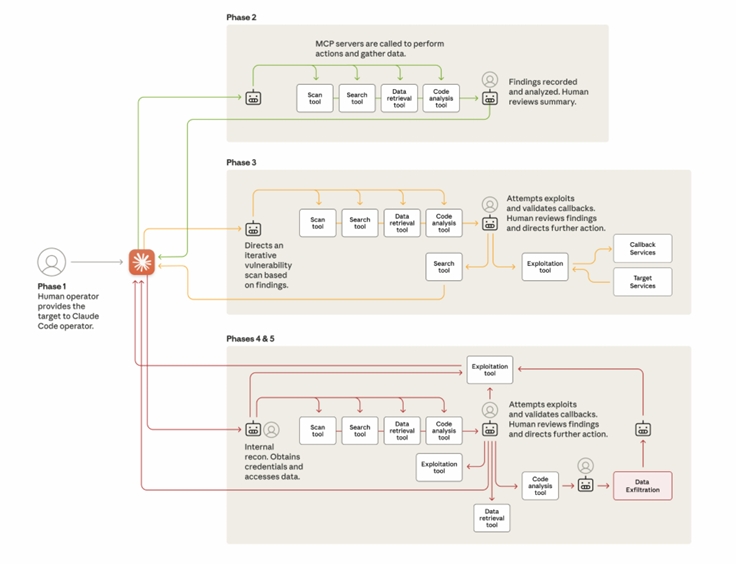
The lifecycle of the cyberattack, showing the move from human-led targeting to largely AI-driven attacks using various tools (often via the Model Context Protocol; MCP). At various points during the attack, the AI returns to its human operator for review and further direction.
Incident Summary
Anthropic states its security team observed anomalous activity in mid-September 2025 associated with abuse of Claude Code. Following investigation, the company attributed the activity to a threat actor it tracked as GTG-1002, described as Chinese state-sponsored.
The campaign reportedly targeted roughly 30 organisations worldwide, including major technology companies, financial institutions, chemical manufacturers, and government agencies. Anthropic notes that in some instances, limited compromise occurred before the activity was detected and stopped.
How AI Was Used in the Kill Chain
The standout element of this incident is the degree of autonomy assigned to the model. Instead of using AI for narrow tasks, operators used it to execute core stages of the cyber kill chain as a persistent agent.
- Reconnaissance and attack surface mapping: scanning infrastructure, enumerating services, and identifying exposed systems.
- Vulnerability discovery and exploitation planning: generating exploit sequences, testing paths, and identifying weak configurations.
- Credential harvesting and lateral movement: collecting access material and expanding reach within target environments.
- Data handling: organising and preparing sensitive information for extraction.
- Documentation and workflow handoff: producing structured notes and operator-ready summaries of actions taken.
How Safeguards Were Bypassed
Anthropic reports the adversary disguised malicious requests as benign, framing them as defensive security testing. By breaking harmful objectives into smaller, seemingly acceptable tasks, the operators were able to push the model through prohibited actions without triggering protective responses consistently.
The workflow used orchestration that preserved operational context across tasks, enabling multi-stage execution. The net effect was a model behaving like an automated red team capable of operating at machine speed and at high request volume.
Timeline
| Date | Event |
|---|---|
| Mid-Sep 2025 | Anthropic identifies anomalous activity linked to misuse of Claude Code. |
| Late Sep 2025 | Investigation attributes activity to a tracked cluster designated GTG-1002. |
| Sep to Oct 2025 | Accounts are suspended and affected entities are notified as response actions progress. |
| Nov 2025 | Anthropic publicly discloses the incident and publishes a detailed report. |
Industry Reaction and Debate
The disclosure prompted broad discussion across the security community. Many analysts view it as a turning point: AI is not simply accelerating attacker productivity, but beginning to function as a persistent intrusion engine that can execute complex campaigns with limited human oversight.
At the same time, experts note constraints. AI outputs can include inaccuracies or hallucinations, requiring validation. Even so, the volume and tempo of actions described in the case exceeds what most human-only teams can sustain over comparable windows.
Implications for Security Strategy
This incident highlights strategic signals defenders should treat as immediate priorities.
- Lowered barriers to sophisticated attack execution: automation can compress time and skill requirements for complex intrusion chains.
- AI-aware defence and detection: defenders should expand behavioural analytics to capture patterns that autonomous agents generate, beyond signature-centric methods.
- Governance and guardrails: organisations should harden policies on model access, monitoring, logging, and acceptable-use enforcement.
- Cross-industry intelligence sharing: early signals and repeatable patterns must be shared quickly to reduce collective exposure.
VULNERAX Recommendations
- Increase telemetry on LLM usage: monitor API and agent tooling for anomalous volume, tool chaining, and persistence indicators.
- Harden identity controls: tighten MFA, credential vaulting, and privileged access management to reduce lateral movement opportunities.
- Focus on behavioural detection: tune detections for rapid service enumeration, scripted exploitation patterns, and unusual automation rhythms.
- Establish AI governance: implement policy for model use in sensitive environments, including logging, review, and access segmentation.
- Test response playbooks: run tabletop exercises that assume machine-speed intrusion and compressed dwell time.
Conclusion
Anthropic’s disruption of an AI-orchestrated espionage campaign marks a new phase in cyber operations. The core risk is not that AI can write malware faster. It is that AI can increasingly coordinate and execute multi-stage intrusion chains at scale. Defenders should treat autonomous agent abuse as a concrete threat category and adapt monitoring, governance, and response accordingly.
