Introduction
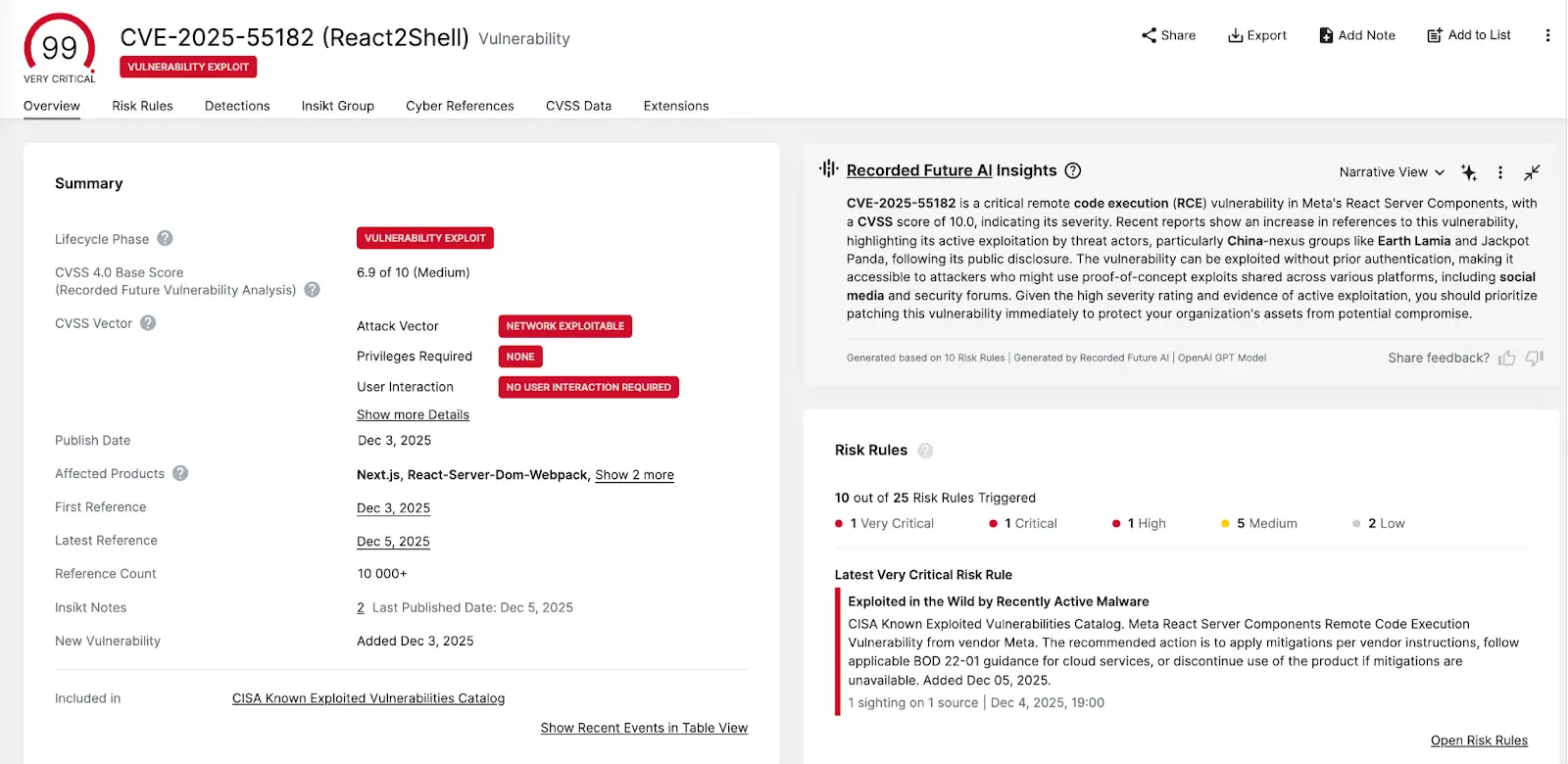
A newly disclosed, high-severity vulnerability affecting React Server Components (RSC) has sparked immediate global concern within the cybersecurity community. Known as React2Shell (CVE-2025-55182), it is actively exploited by Chinese state-linked threat operators.
With widespread adoption of React frameworks like Next.js, Waku, and React Router, VULNERAX urges organizations to urgently assess and patch affected systems.
CVE-2025-55182 (React2Shell) Intelligence Card®
Overview of the React2Shell Vulnerability
Rooted in unsafe deserialization of React Server Function endpoints, this vulnerability enables attackers to execute arbitrary backend code through crafted HTTP requests.
Affected versions include:
- React Server Components 19.0
- 19.1.0 and 19.1.1
- 19.2.0
This flaw extends its reach beyond React core to many dependent libraries and frameworks.
Active Exploitation and Attribution Claims
On December 4, AWS Threat Intelligence reported ongoing exploitation linked to threat groups such as Earth Lamia, Jackpot Panda, and other unclassified Chinese clusters.
Recorded Future’s Insikt Group links IP 143[.]198[.]92[.]82 to HiddenOrbit, a known Chinese relay infrastructure used to mask offensive activities consistent with APT tactics.
Scope and Impact: A Rapidly Growing Problem
According to Wiz Security, 39% of scanned cloud workloads contain vulnerable React deployments, with near 100% exploitation success due to predictable deserialization flaws.
Vulnerable ecosystems include:
- Next.js
- React Router
- Waku
- Redwood SDK
- RSC plugins for Parcel and Vite
Attack Timeline
| Date | Event |
|---|---|
| Dec 3, 2025 | React Team publicly discloses CVE-2025-55182 and issues patches. |
| Dec 3, 2025 | Recorded Future releases attack-surface detection signature. |
| Dec 3, 2025 (10:00 PM UTC) | DataDog detects 80+ threat actor–linked IPs scanning globally. |
| Dec 4, 2025 | AWS announces active exploitation by Chinese groups. |
Proof-of-Concept Exploits in the Wild
Several PoC exploits have appeared. The most acknowledged was published by Lachlan Davidson, demonstrating multipart/form-data POST requests crafted to emulate server action calls, leading to arbitrary code execution.
However, many circulating PoCs are unreliable or require unrealistic setups, as pointed out by AWS and Davidson.
Immediate Actions Required
Organizations using React stacks should:
- Identify Vulnerable Assets: Use scanners like Assetnote’s react2shell-scanner, npm audit, or Insikt Group’s Nuclei detection template.
- Apply Security Patches: Update React and Next.js to patched versions 19.0.1, 19.1.2, and 19.2.1.
- Block Known Malicious IPs: Temporarily block IPs like 143[.]198[.]92[.]82, 206[.]237[.]3[.]150, 45[.]77[.]33[.]136, and 183[.]6[.]80[.]214 to reduce exposure.
Why CVE-2025-55182 Is High Risk
The convergence of state-sponsored exploitation, reliable exploits, broad adoption, multiple PoCs, rapid weaponization, and widespread unpatched deployments make this vulnerability exceptionally dangerous.
VULNERAX Recommendations
- Prioritize patching above all else, not relying solely on detection.
- Audit all public-facing React/Next.js infrastructure, including microservices.
- Harden CI/CD pipelines to prevent redeployment of vulnerable versions.
- Enable WAF rules blocking suspicious multipart POST requests targeting RSC endpoints.
- Monitor threat intelligence feeds actively for new IoCs and exploitation trends.
Conclusion
CVE-2025-55182 represents a critical threat to the modern JavaScript ecosystem, with advanced Chinese actors exploiting widespread vulnerable deployments. Immediate remediation is vital.
